CSE 523 – System Security
System Security代写 Homework #1
System Security代写 The purpose of the homework is two-fold. First, by following the steps below, you will prepare your computer for the…
The purpose of the homework is two-fold. First, by following the steps below, you will prepare your computer for the work we will be doing in CSE 523 this semester. Second, you will begin the habit of keeping careful, repeatable notes to document your work.
Your homework submission will be a report describing the steps you took to download, install, and configure SEEDLabs 16.04-32bit VM on your computer. You should configure your VM so you’d be able to copy and paste it to and from your host machine. We also ask that you configure ~/.bashrc to display the date and your name in the terminal prompt, as shown in the screenshot below: System Security代写
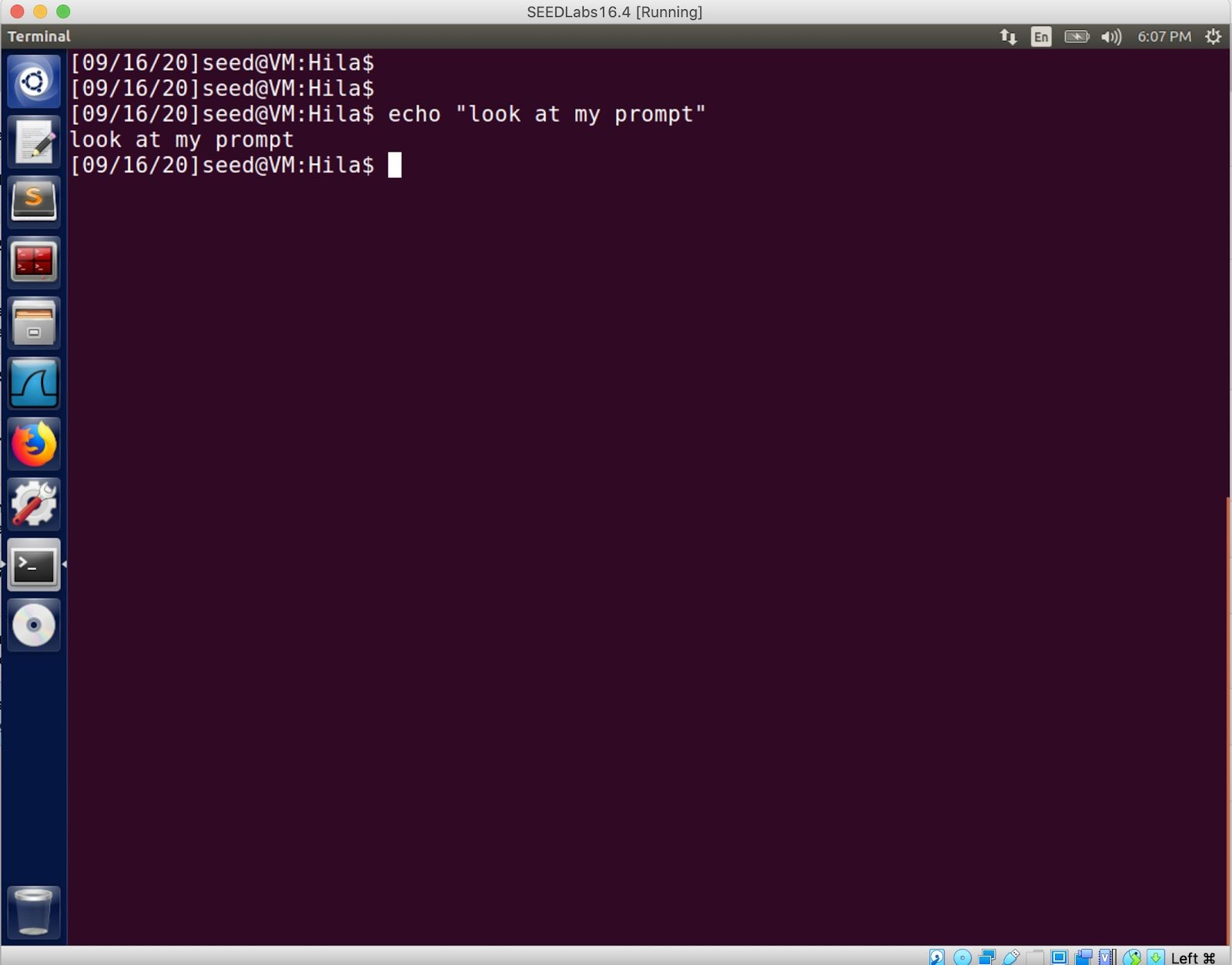
Figure 1: Prompt displaying date (9/16/20) and name (Hila). System Security代写
You can display your first or last name, or a combination of the two. When done, please take a snapshot of your VM as it is sometimes helpful to have a working backup in case something goes wrong. Please read this if you need to learn more about snapshots.
Grading rubrics System Security代写
It is possible that this is the first time you are asked to write a report like this. It can be tricky at first, but you will get better as you practice. We provide the grading rubric below to give you a sense of what we are looking for in the report. You can see that the grading rubrics correspond to the general homework instructions we gave in the second paragraph. Keep that in mind when working on future homework assignments.
This homework assignment is worth 5 points with the following break down: System Security代写
| Possible points | Rubric |
| 2 | Successful installation and configuration of the VM.
You must include a screenshot showing your prompt to get this credit. |
| 1 | A snapshot was taken. Take a screenshot of your snapshot. |
| 2 | Sufficient documentation and repeatable notes. Hence, someone* else can reproduce your work.
*someone else refers to another student taking this course, not a random person who never used a computer before. You don’t have to provide basic instructions such as how to open a browser or how to open a folder. |
Learning how to document your work will serve several ends. First, it will function as your turn-in for homework this semester. Second, it will allow the TA and I to help you whenever you need it, and to see exactly where you are stuck; Third, security work requires a systematic, patient, and detail-oriented mindset, and maintaining your notes in this way will get you started down this path (if you aren’t on it already).
Tips and pointers System Security代写
Configuration tips:
- Youcan find SEED Lab configuration guidelines here.
- Note:you do not have to follow all the steps in this document, but you would want to pay attention to the ‘Bidirectional’ configuration. You should probably also change the Graphics Controller to VBoxVGA. System Security代写
- Donot copy the instructions from the Use your own words and voice. It is recommended, but not required, to write in first person.
- Ifyou already have the latest version of VirtualBox installed, you don’t need to reinstall Instead, explain that you have it. If you don’t have VirtualBox installed, make sure to describe the steps you take in your report.
- “source~/.bashrc” may be a useful Report tips:
- Whendescribing your steps, it can be helpful to include You should ask yourself whether an instruction can be clearer if it is accompanied by a screenshot. Please do not include a screenshot for every step you take! Your words and description are important.
- You can include screenshots in two easy steps. System Security代写
- Capturethe window/screen you On Windows, select your window, press Alt-PrtSc. On Mac, press shift-control-command-4 and then draw a rectangle around the area you want to copy. Once you have the image in your clipboard, you can copy-paste it into this document; once the image is in the document, you can crop or resize as needed.
- Createa table to hold the image and Use Table->Insert table to add a 1-column, 2-row table. Copy-paste your image into the top row; resize the image so that it fits on your page. Add your caption to the second row in the table. Use Table->Table properties to set the table border to 0 pt, unless you like seeing the grid lines.
- Your report doesn’t have to be lengthy to be Try to be concise but informative. System Security代写
You can find an example of a partial report from an old offering of the course below. Please note that it uses a different VM setup, so DO NOT follow these instructions. We use this only as an example to give you a sense of a good writeup.
EXAMPLE
1. Install VirtualBox System Security代写
Install the latest version of VirtualBox (6.1.2 as of January 2020) on your computer. If your CPU supports VT-x or AMD-v, you may need to enable it. (Note that sometimes you have to make a change to my laptop’s BIOS, power down, remove the battery (!), replace the battery and then reboot for VT-x to be enabled.) Mine was already enabled.
2. Create a new Ubuntu Virtual Machine
We will create an Ubuntu virtual machine in this section.
Download the Ubuntu 14.04.6 LTS Desktop.iso (Use the 14.04 64 bit desktop version) file at the linked URL. Feel free to view the alternative downloads if you’d like to torrent the download. Also, while it is nice if you want to donate, please note that it is freely provided if you click Not now, take me to the download! at the bottom of the contribute page.
In this document, you will learn to configure a virtual machine from an image format like .iso. Here are the guidelines for once you’ve downloaded the .iso file: System Security代写
- OpenVirtualBox
- Clickthe “New” icon
- Entera name for your VM and select the proper type and version.
a.If you name it something with “Ubuntu”, the type and version will be automatically - On the next screen, enter the amount of RAM you want to dedicate to the virtual You are welcome to do more, but at least 1024 MB is strongly recommended.
- Onthe next screen, we will create a virtual hard disk now.
- Select.vmdk as your
- Dynamicallyallocated is Please do 20 GB.
- Afterthis, your virtual machine should be created, but it is not configured for use.
To configure the virtual machine: System Security代写
- Selectyour newly created virtual machine and click “Settings”.
- Under“Storage”, select the Empty disk under “Controller: IDE”
- Clickthe CD image next to “Optical Drive: IDE Secondary Master” and select “Choose Virtual Optical Disk File”
- Navigateto your Ubuntu 04 .iso file and select open. System Security代写



