31
3月
Critical Infrastructure代写 National代写
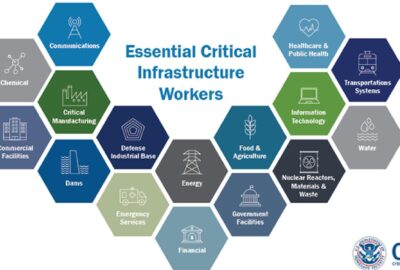
CYBER VULNERABILITIES Name Course Date National Critical Infrastructure Critical Infrastructures are…

CYBER VULNERABILITIES Name Course Date National Critical Infrastructure Critical Infrastructures are…