Vulnerability Assessment of GeeGee Internet and Data Solutions
by (Name)
Introduction to Risk and Due Diligence
Tutor
Swinburne University of Technology
1.Vulnerability Assessment
Vulnerability Assessment代写 Involves discovering vulnerabilities with aims of reducing them and increasing the ability to manage them in future.
GeeGee Internet and Data Solutions
GeeGee is a medium-sized enterprise at its start-up stage. The company is a partnership between me and close friends. We offer data storage and web hosting services to our clients. Our main objective is to provide a platform where clients rent a domain to host their websites and cloud storage services and retrieve data from our servers.
We decided to do vulnerability assessment on our company to identify the likely risks and hazards that might pose vulnerabilities. This is important decision to make especially for our young company. The test helps establish the threats and vulnerabilities that need to be addressed in present and future. When we establish our weaknesses, we will be able to work on them to reducible minimums for the betterment of the company.
Vulnerability assessment involves discovering vulnerabilities with aims of reducing them and increasing the ability to manage them in future. There are various risk assessment techniques but in our case, we will use Failure Mode and Effect Analysis (FMEA). This technique identifies potential failures and tries to figure out what effect failures would have.
Key success factors Vulnerability Assessment代写
The core assets that our company put effort into this vulnerability analysis are the customers, data warehouses, employees, data security, web securities and market competitiveness.
i.
Customers focus – customer service is our key priority. Our customers need better services compared to other companies offering similar services. The reason why customers focus is key to our success is because we are offering a service which must meet customer’s specification and specific needs, and also because they have market choices to make. So we must give them a reason to choose us over our competitors.
ii.
Data Security – investing in data security is paramount to build our company reputation and also create good relation with our customers. Our clients need privacy assurance(Calder and Moir, 2009)for their data with us, therefore this is also one of our main area of focus for market competitiveness.
iii. Vulnerability Assessment代写
Investment in automation – we tend to use a variety of open-source and in-house management and monitoring tools. To increase speed and time and reduce costs we need to invest in more advanced management and monitoring tools. The reason for choosing this as the asset of success is because our main service foundation is machines and computers. Therefore automation of various services will be inevitable.
iv.
Accessibility guarantee – we need to assure our clients that our services will be 100% accessible and available online. The reason this is as a success factor is because our clients hold confidential information with us which they may be needed anytime anywhere. We need them to trust us on this by providing 24/7 access and retrieval.
v.
Talented and passionate man-power – we not only attach our success on trained people, we also hunt for talents and passion in computing. We believe people who are passionate and talented in computing offer bigger value to our company. We recruit and train them according to their area of interest.
Threats Vulnerability Assessment代写
These are events that pose some harm to the company and its resources if not addressed early.
a.
Password security – our staffs can easily be tricked to provide access to the servers. In such case, the attackers are likely to use keyloggers or inject malicious codes into their computer systems which will expose security measures of the company. This will expose our clients’ data which is supposed to be protected at all costs. On the other hand, our clients are also vulnerable to attacks if they fail to take necessary security measures to protect their systems. These attacks can expose their passwords and important information on our servers in which their information is held (Wee, 2012).
b.
Physical security – our servers and data storage are housed in a warehouse. Although we have installed 24 hours security watch, which does not totally eliminate physical access to our data center or other risks (Al‐Awadi and Saidani, 2010).
c. Vulnerability Assessment代写
Competition – the company is competing in a service market. The competition is high and customers are looking for quality, affordability, accessibility, convenience, and timely services.
d.

Data and server security – computer advancement and speed have come with it good and bad sides. The bad side of it is information security mostly the fear of losing data to malicious people. Cyber-crime is at an increasing trend and this has affected our company (HM Government UK, 2014).
e. Vulnerability Assessment代写
Privacy issues (Hayhurst, 2014) – today companies are using data centers uploading sensitive and confidential data. They need to be sure that no one is viewing their information, or use it information whatsoever without their consent. Any customer information leak is detrimental to our business and company reputation.
f.
Hacking – computer age has grown and many people are becoming computer enthusiasts who are ready to explore the world of computation to their own limits. This has created a group of people who look to enter into any computer systems for maliciously for fun (Goel and Mehtre, 2015)
g. Vulnerability Assessment代写
Endangerment of high-level management staff – our company store confidential and other important data from our clients. The information we store may endanger our key employees who are responsible to maintain data servers. The information we hold for the client may have interest groups who can do anything to gain access to such information.
h.
Ineffective monitoring of individuals in data center area – one computer room in a data center covers a large area, with storage devices arranged next to each other. These storage devices are managed by separate personnel. Therefore it has become difficult to manage and track them once they have access to these areas (Mocydlarz-Adamcewicz, 2011).
i. Vulnerability Assessment代写
Undetected smoke – sometimes there is fire outbreak caused by power surge by storage apparatus. We have installed fire alarms in the facility but resulting smoke may be undetectable by our standard smoke alarms, let alone the human eyes because it is often too fine and in small quantity. Advanced alarm systems need to be installed to mitigate this threat.
j.
Natural disaster – disasters like torrential rains, floods, earthquakes, and winds are likely to cause destruction to our data facility. Our structures are not built to withstand some of these disasters when they occur.
Methods of selection Vulnerability Assessment代写
Our responsibility was to identify threats affecting the company. Threats posed danger to our company success. To be able to select these threats we used employees provided information on their stations, evaluated occurrences books, we also did a physical audit of the company facilities. Some threats to the data and servers which are not easily identifiable, we had to run vulnerability testing tools on the computers and data servers. The threats identified are the one that has occurred or was prevented from occurring. There these threats are critical to the management so that relevant actions and responses are taken.
Critical Vulnerabilities Vulnerability Assessment代写
These are deficiencies the company whose occurrence leads to the materialization of the threats.
a.
Remote code execution – we found that an attacker will be able to run arbitrary, system-level code on our server. The problem was caused by improper coding. We were able to detect this problem after carrying out source code review. We found out that the vulnerability will allow an attacker to exploit register globals in PHP and use XMLRPC for PHP vulnerabilities. This vulnerability posed total system compromise and damage to servers.
b.
The company also lacked proper differentiation in the market. This posed a risk of losing customers to competitors. We needed to offer a product package that is distinct and acceptable in the market.
c. Vulnerability Assessment代写
The facilities lacked high-quality alarm systems, not enough strategic surveillance cameras, and lack biometric identification system of the workers for easy control of entry.
d.
The data warehouse was not properly designed and built to withstand all weather conditions and a natural disaster. The building is built on a power drainage area, therefore, increased chances of flooding.
e. Vulnerability Assessment代写
Lacked effective firewalls to detect and block attacks. We were able to access servers from a remote computer using vulnerability testing tools (Goel and Mehtre, 2015). This means the whole system was vulnerable to external attach which might be malicious.
f.
Employees’ vulnerability – using our system, was able to trick some employees and was able to access information through their system. This demonstrated the ignorance with some of them which posed a potentially higher risk which can be used by attackers.
2.Precautionary Analysis Vulnerability Assessment代写
To carry out precautionary analysis we will use Failure Mode Effects Analysis (FMEA) (Stamatis, 2003). This technique uses a step-by-step approach to identify possible failures in the company services.
“Failure modes” means the ways in which service might fail. Failures are any faults, particularly ones that affect our customers or can be potential or actual.
“Effects analysis” refers to studying the significances of those failures.
Under this his technique, failures are ranked according to how serious their consequences are, how often they occur and how their detectability. The purpose of the FMEA is to take actions to reduce or eliminate failures, starting with the highest-priority ones.
| Key success factor/ function | Potential failure mode | Potential effects of vulnerabilities | Potential cause(s) of failure | Precautionary recommendation |
Customers focus |
Lack quality data and internet services | Losing customers to the competitors | System lag and failures | Installation of advanced apparatus |
Data security Vulnerability Assessment代写 |
Vulnerable database algorithms and codes | Data leak, device failure, loss of company reputation | Hacking
Injection of malicious codes |
Software reviews and building patches and updates in the system |
Investment in automation |
Slow services to our customers | Poor response to customers’ needs | Lack of finance | Invest in automation most critical services with latest advanced tools |
Talented and passionate workers Vulnerability Assessment代写 |
Lack of motivated workers
Employees vulnerability |
Poor production,
Poor customer services, High turnover rate. |
Recruitment and selection failure,
Ineffective organization structure |
Invest in workers training, development and motivation.
Proper recruitment and selection criteria |
Accessibility guarantee |
System failures
Damages by natural disasters Accidents Data loss |
Dissatisfaction of our customers
Data loss Apparatus damages Loop-holes for data theft |
Poor construction and design
Lack of advanced alarm systems Lack back up system |
The building of an all-weather warehouse
Advanced alarm systems Having back up option installed
|
Competition Vulnerability Assessment代写 |
Poor market targeting
Lack of differentiation Lack of advanced tools |
Losing customers to competitors
Loss of market Loss of revenues Stagnation
|
Our service lack differentiation
Targeting larger market Poor apparatus |
Implement services differentiation in the market
Invest in better technology |
The high-level management staff |
No measures are put in place to protect staff | Endangered their lives | Fear for their life
Low motivation to work for us |
Equipped them with wireless emergency alarm apparatus that send an emergency alarm signal that can notify security guard staff to enact any necessary measures.
|
Monitoring Vulnerability Assessment代写 |
Uncontrolled access to some company facilities
Poor control of workers in the warehouse |
Tampering with data and servers
Access to malicious software to the data server and system |
Loss of client data
Data Leaks Damage of apparatus Hacking |
Installation of employee monitoring tools like biometric log systems, movement detectors, CCTV, and train employees on standards measures for protecting the facility |
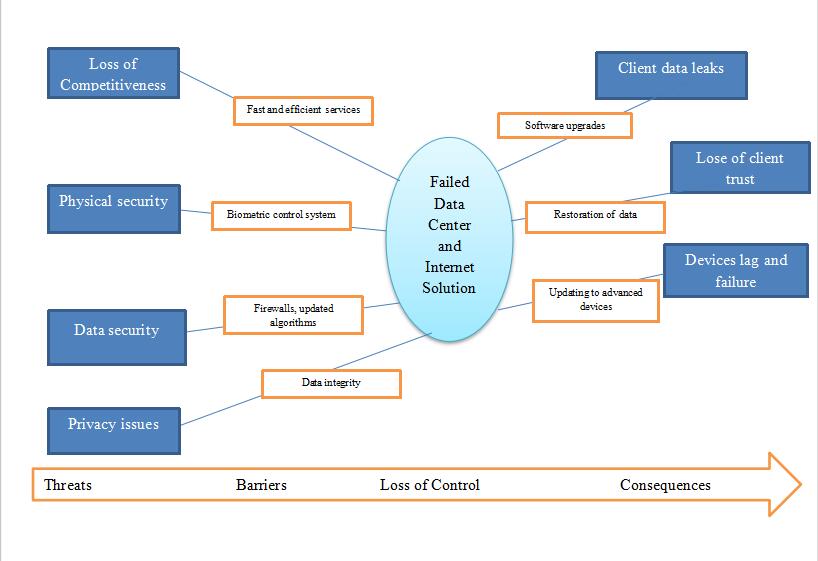
Threat Barrier Diagram – GeeGee Data Center and Internet Solution
References
Goel, J. and Mehtre, B. (2015). Vulnerability Assessment & Penetration Testing as a Cyber Defence Technology. Procedia Computer Science, 57, pp.710-715.
HM Government UK (2014). Cyber Essentials Scheme Requirements for basic technical protection from cyber attacks.
Hayhurst, C. (2014). Is Your Patient Data Secure?. Biomedical Instrumentation & Technology, 48(3), pp.166-173.
Wee, H. (2012). Public Key Encryption against Related-Key Attacks. George Washington University.
Mocydlarz-Adamcewicz, M. (2011). Practical guidance on implementation of the Personal Data Security Management System in an oncology center. wo, 5, pp.279-285.
Al‐Awadi, K. and Saidani, M. (2010). Justifying the need for a data security management plan for the UAE. Info Mngmnt & Comp Security, 18(3), pp.173-184.
Calder, A. and Moir, S. (2009). IT governance. Ely, UK: IT Governance.
Stamatis, D. (2003). Failure mode and effect analysis. Milwaukee, Wisc.: ASQ Quality Press.
更多其他:cs论文代写 Essay代写 Proposal代写 人文社科代写 文学论文代写 心理学论文代写 哲学论文代写 艺术论文代写 商科论文代写 学术代写 Report代写 Case study代写 网课代修 代写论文 艾莎代写 研究论文代写 Admission Review代写 Academic代写